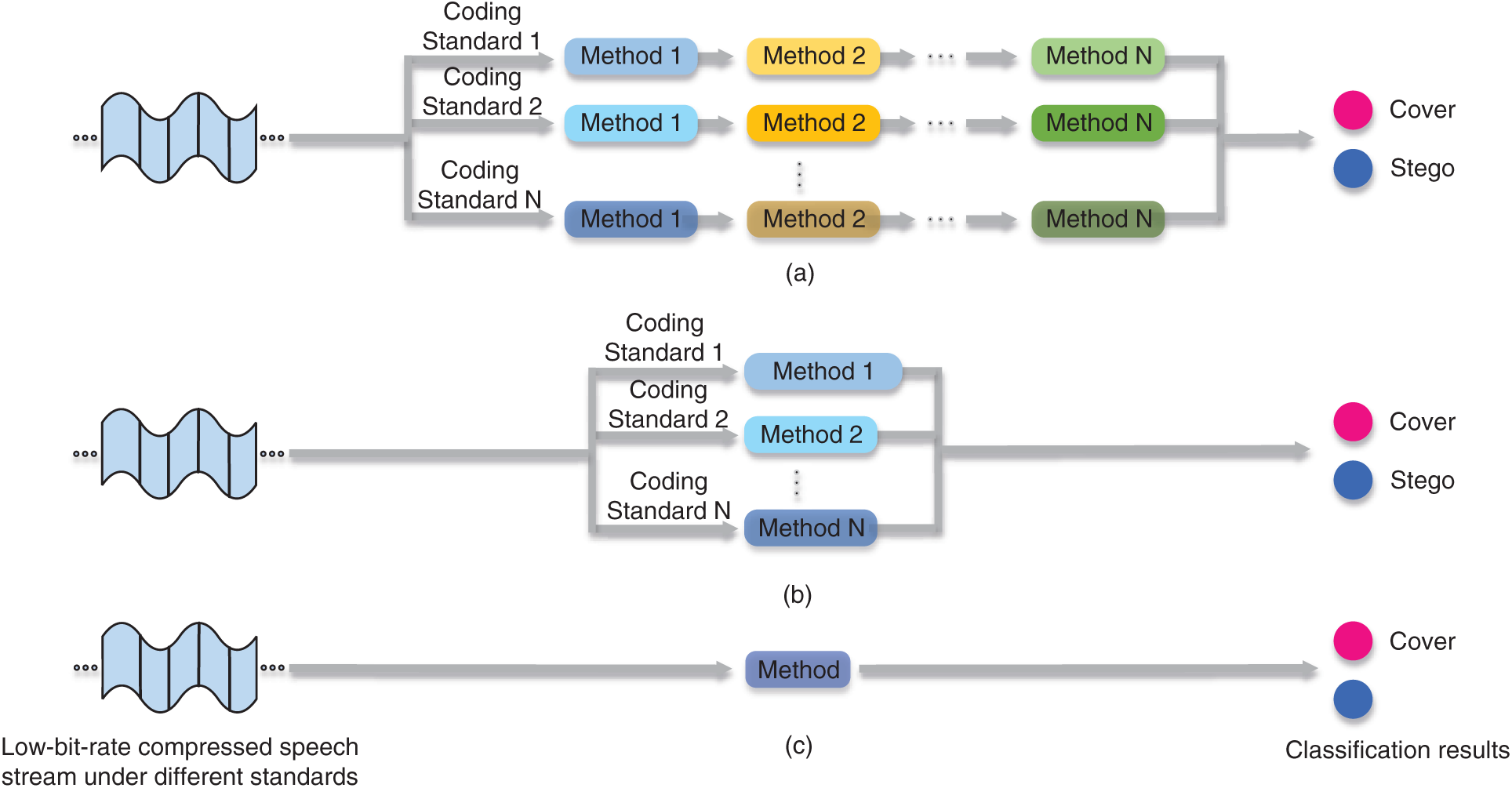
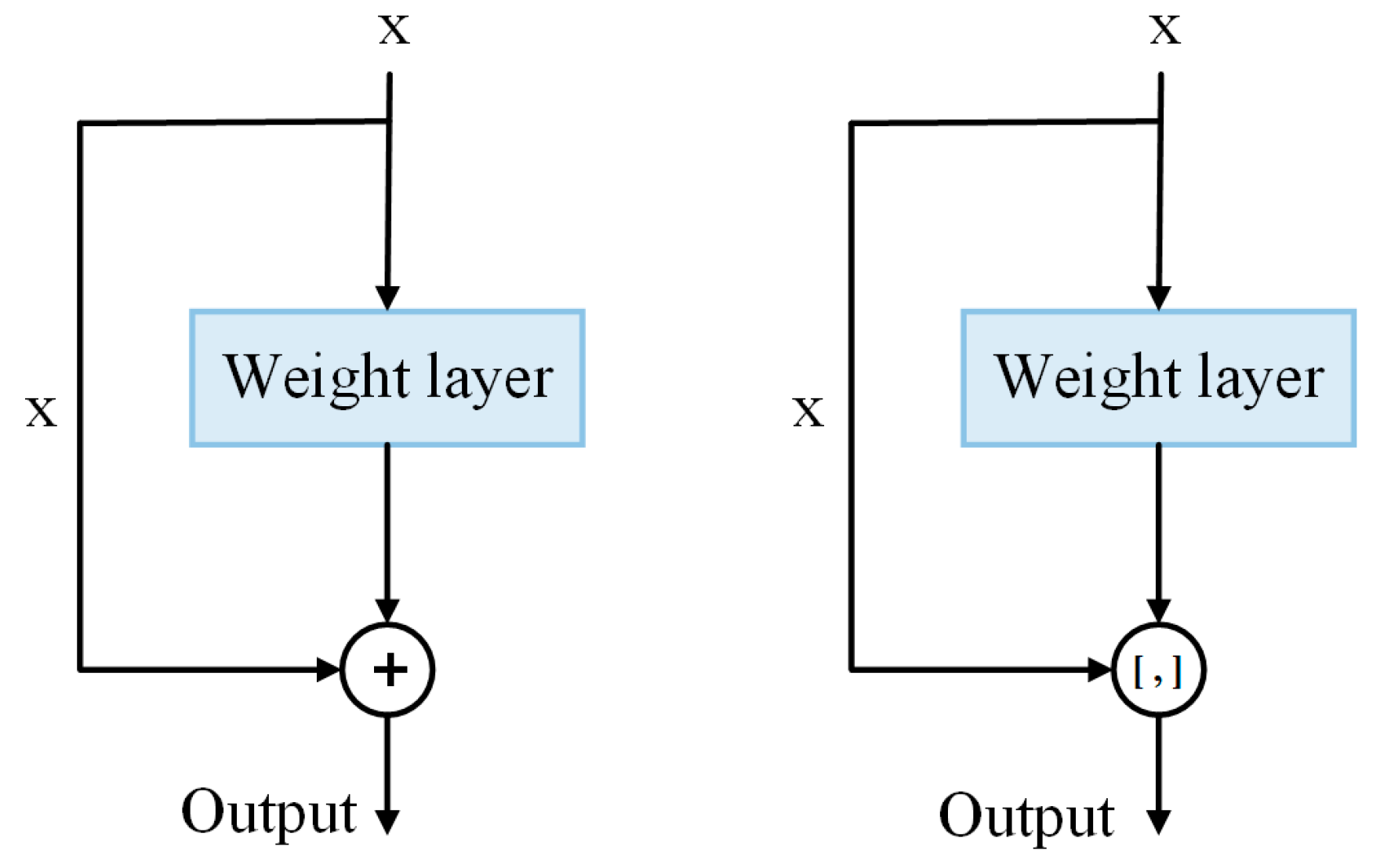
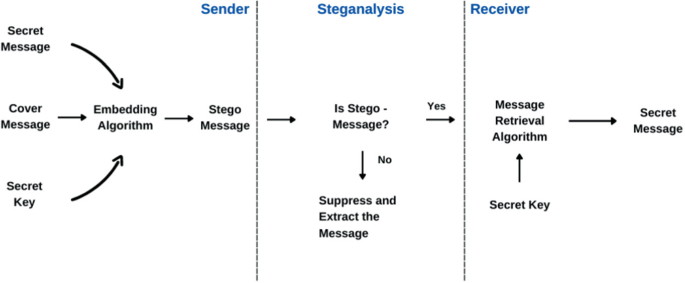
Steganalysis performance under different speech lengths with 20 ms per... | Download Scientific Diagram

PDF) Steganography and steganalysis: data hiding in Vorbis audio streams | jesus diaz - Academia.edu

Intra Block and Inter Block Neighboring Joint Density Based Approach for Jpeg Steganalysis by ijscjournal - Issuu

Barplots of the distribution of guesses divided into the 10 songs in... | Download Scientific Diagram

A comprehensive review of video steganalysis - Bouzegza - 2022 - IET Image Processing - Wiley Online Library
Steganography - A review Lidan Miao 11/03/03. Outline History Motivation Application System model Steganographic methods Steganalysis Evaluation and benchmarking. - ppt download